The forest is at the top of the AD DS hierarchy
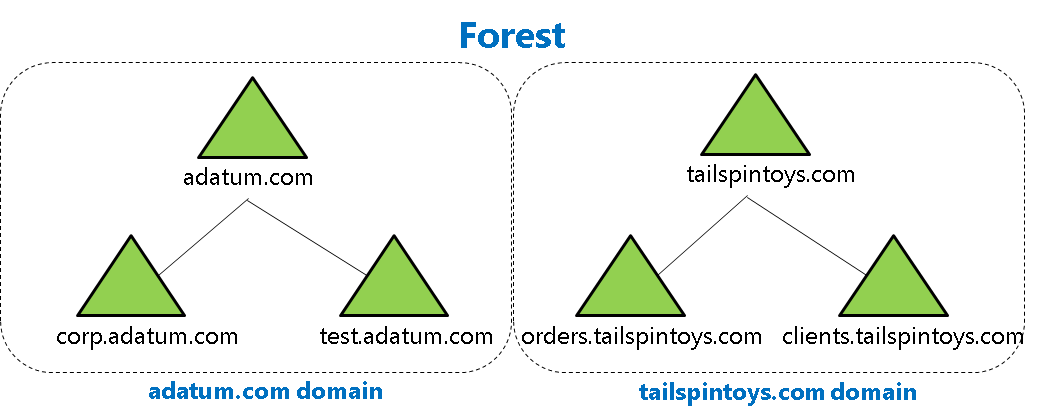
An AD DS forest is the highest-level container object in the AD DS hierarchy. A forest is a collection of one or more AD DS trees. Each AD DS tree will contain one or more AD DS domains. The AD DS forest is the outermost boundary for the AD DS security and administration.
The forest root domain is unique
The first domain that is created in the forest is called the forest root domain. The forest root domain contains a few objects that do not exist in other domains in the forest. Because these objects are always created on the first domain controller created, a forest can consist of as little as one domain with a single domain controller, or it can consist of hundreds of domains across multiple trees.
What are flexible master operation (FSMO) roles?
FSMO roles are special roles within a forest and domain. There are five roles, two of which are at the forest level. let's look at the forest FSMO roles in the forest root domain.

The schema master role.
This is a special forest-wide domain controller role. There is only one schema master in any forest. The schema can be changed only by targeting the domain controller that holds the schema master.
The domain naming master role.
This is also special forest-wide domain controller role. There is only one domain naming master in any forest. New domain names can be added to the directory only by the domain naming master.
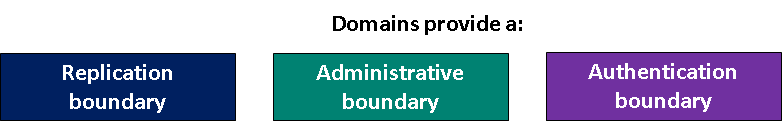
The forest is a replication and security boundary

The forest is a security boundary
A forest is often referred to as a security boundary because it provides the most complete and secure separation of Active Directory domains.
By default, all the domains in a forest trust the other domains in the forest automatically. This makes it easy to enable access to resources such as file shares and websites for all users in a forest, regardless of the domain in which the user account is located. However, no users from outside the forest can access any resources inside the forest.
A forest is a replication boundary
A forest is also referred to as a replication boundary for the configuration and schema partitions in the AD DS database. It is also the replication boundary for the global catalog. This means that all domain controllers in the forest must share the same schema.
Typically, an organization creates only one forest, although you can create multiple forests to isolate administrative permissions between different parts of the organization.



What is Privileged Access Management?
Privileged Access Management (PAM) for Active Directory Domain Services is a solution that is based on Microsoft Identity Manager (MIM) and Windows Server 2012 R2 and Windows Server 2016. It helps organizations restrict privileged access within an existing Active Directory environment.
How does PAM work?
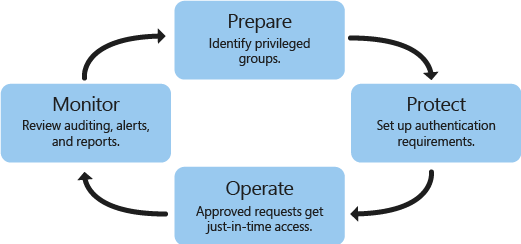
PAM uses a new bastion Active Directory forest that has a trust with your existing forest. The bastion forest establishes a pristine environment that isolates the use of privileged accounts and reduces the corresponding risk of those credentials being stolen. PAM provides authentication requests as they are needed, and adds auditing, alerts, and reports of privileged access requests.
PAM does not require any changes to existing applications or users in the Active Directory environment. There is no need to upgrade any servers or raise the domain or forest functional levels in that environment to get started using PAM.
What are Domains and Forests? - This technical reference covers the logical and physical Active Directory structure, as well as domains and forests.
Privileged Access Management for Active Directory Domain Services - This article covers the problems that PAM solves, how PAM is set up, and how PAM works to secure privileged accounts.